Security Group
Description
A Security Group is a simplified packet-filtering firewall, helping you to control the traffic through your infrastructure
Note that this basic level security is a first and mandatory step to make an infrastructure secure, it should not be considered as sufficient security for building a secure infrastructure
Please, start by reading this article), if you would like to know more about firewalling and security
A Security Group is composed of one or more instance(s), and a set of rules
The rules can filter the incoming traffic (all Stacks) and outgoing traffic (VPC Stacks only)
The rules can defined as following:
- Incoming/Outgoing traffic
- Source (incoming) or destination (outgoing) IP address or range (CIDR notation, 0.0.0.0/0 for all)
- Source or destination port number or range (1-65535 for all)
- Protocol (TCP, UDP or ICMP)
The following instructions have been realized using a VPC Stack
For a normal Stack, the instructions will be similar, however remember that it is not possible to define outgoing rules in normal Stacks, and we recommend you to setup your own firewall on every instance when using the normal Stacks
Default Security Group
A default Security Group is automatically generated when creating a new Stack
All instances added to this Stack will automatically be placed in this Security Group
You can find and edit the Security Groups in the Stack or the instance properties (right panel)
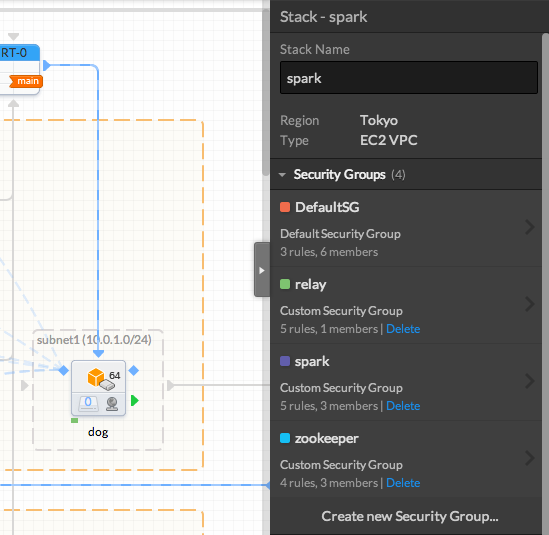
The Default Security Group already contains one rule, allowing all incoming TCP traffic on port 22 (SSH)
This rule is mandatory if you want to manage your instance but you can reduce the IP range if you want to limit the users who can manage your instance
Create a Custom Security Group
If you want to establish different rules for your instances, you need to create some custom Security Groups. You can them define, for each of them, the outgoing and incoming rules
To create a custom Security Group, you can click on 'Create new Security Group' just under the Security Groups list (instance or Stack properties, right panel)
You will be automatically redirected to the rules definition panel
Jump two topics ahead if you want to define your rules now or follow this tutorial and define it later
We created two custom Security Groups for this example
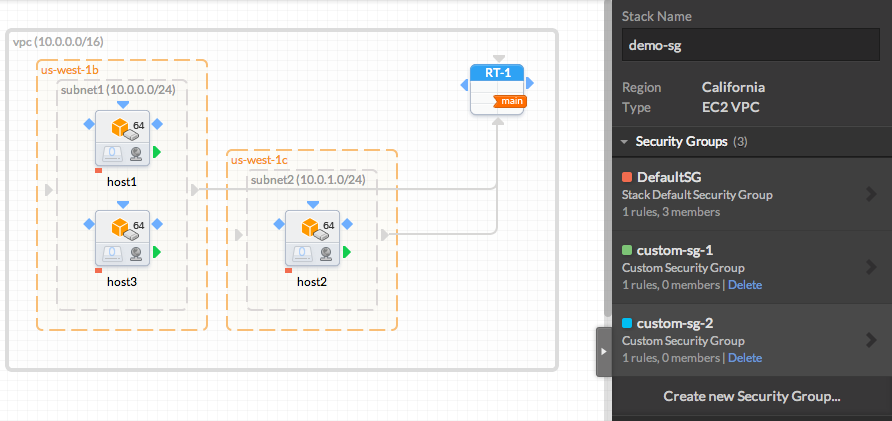
Associate a Custom Security Group
Once the custom Security Group is created, you can now add the instances inside the Security Group
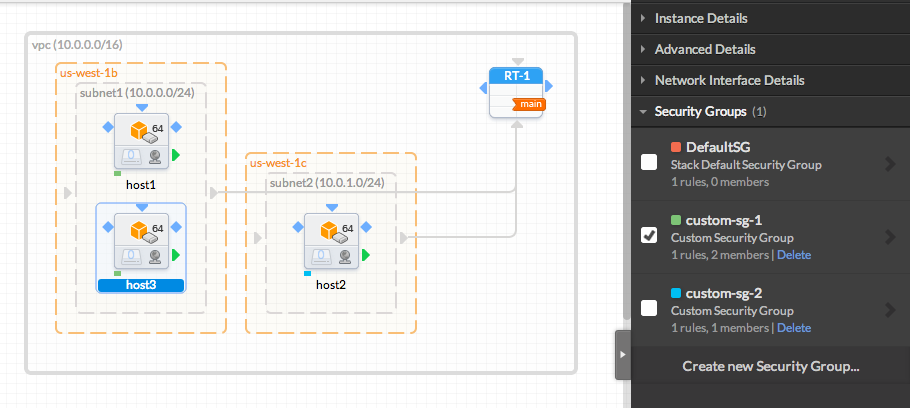
To do so, go on each instances properties, then Security Groups, tick the security group of your choice, then un-tick the DefaultSG
You should see the colored square on the bottom left of your instance change according to the Security Group you are using
Note that an instance can be in several security groups (including the DefaultSG)
See AWS Security Groups documentation for more details about Security Groups themselves
Define Security Rules
You are now ready to create rules in your Security Groups
To do so, click on the right arrow on the right side of the Security Group you want to edit
Once in the Security Group details, click on the + next to 'Rule' to add a new rule, a pop-up will come up
This pop-up allows you to define the following rules:
- Direction (incoming or outgoing traffic)
- Source/Destination
- IP/range (CIDR notation)
- Other Security Group
- Protocol
- TCP: allow all TCP traffic on the selected port/range ("0-65535" for all)
- UDP: allow all UDP traffic on the selected port/range ("0-65535" for all)
- ICMP: select an ICMP packet type to allow (see the list for more details)
- Custom: allow all traffic on a custom protocol
- All: allow all traffic on the selected port/range ("0-65535" for all)
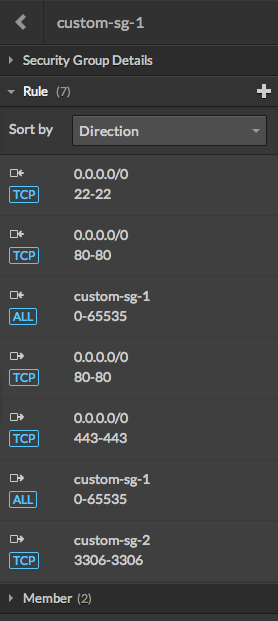
Here is a simple example with two web servers and one database server
We defined the following rules:
| SG | Security Group Rules | |||
| In / Out | Source / Dest | Protocol | Port Range | |
| custom-sg-1 | In | IP range: 0.0.0.0/0 | TCP | 22 |
| IP range: 0.0.0.0/0 | TCP | 80 | ||
| SG: custom-sg-1 | All | 0-65535 | ||
| Out | IP range: 0.0.0.0/0 | TCP | 80 | |
| IP range: 0.0.0.0/0 | TCP | 443 | ||
| SG: custom-sg-1 | All | 0-65535 | ||
| SG: custom-sg-2 | TCP | 3306 | ||
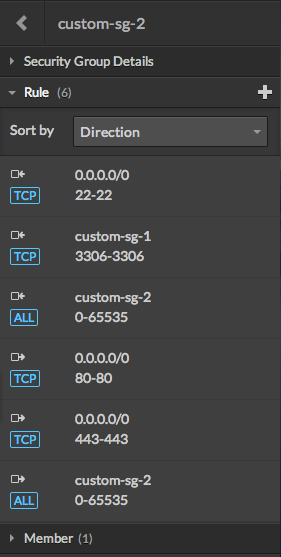
| custom-sg-2 | In | IP range: 0.0.0.0/0 | TCP | 22 |
| SG: custom-sg-1 | TCP | 3306 | ||
| SG: custom-sg-2 | All | 0-65535 | ||
| Out | IP range: 0.0.0.0/0 | TCP | 80 | |
| IP range: 0.0.0.0/0 | TCP | 443 | ||
| SG: custom-sg-2 | All | 0-65535 | ||
Note that you can also link the blue diamonds of each instance to create security rules