VPC with Public and Private Subnets
Description:
The configuration for this scenario includes a virtual private cloud (VPC) with a public subnet and a private subnet. The instances in the public subnet can receive inbound traffic directly from the Internet, whereas the instances in the private subnet can't. The instances in the public subnet can send outbound traffic directly to the Internet, whereas the instances in the private subnet can't. Instead, the instances in the private subnet can access the Internet by using a network address translation (NAT) instance that you launch into the public subnet.
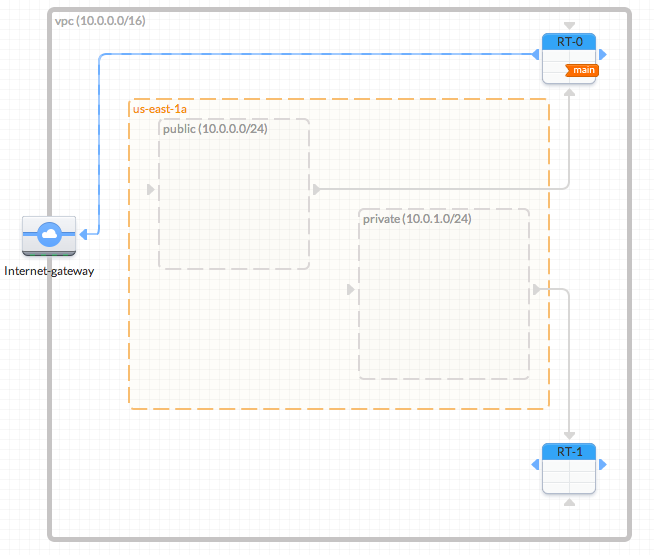
The following diagram shows what we will create in this example:
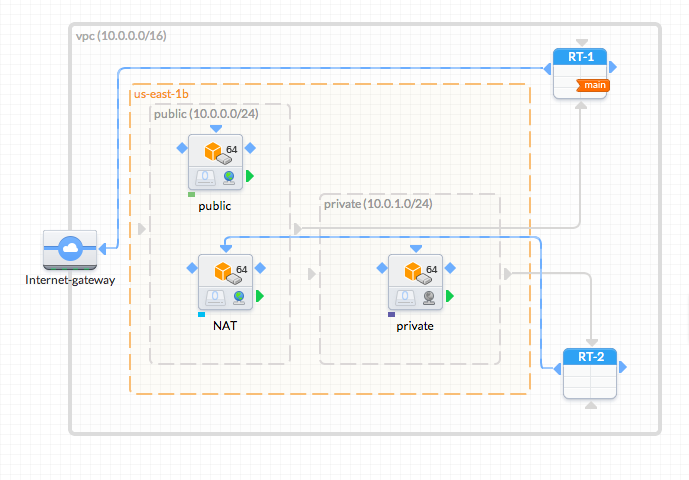
Steps:
- Create a new VPC Stack, in the region of your choice:
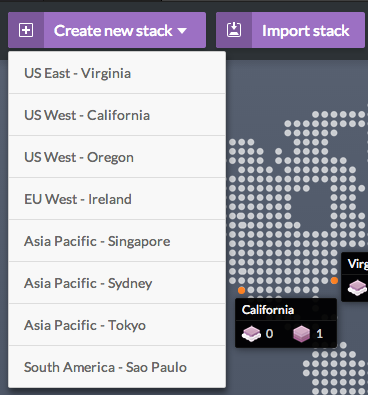
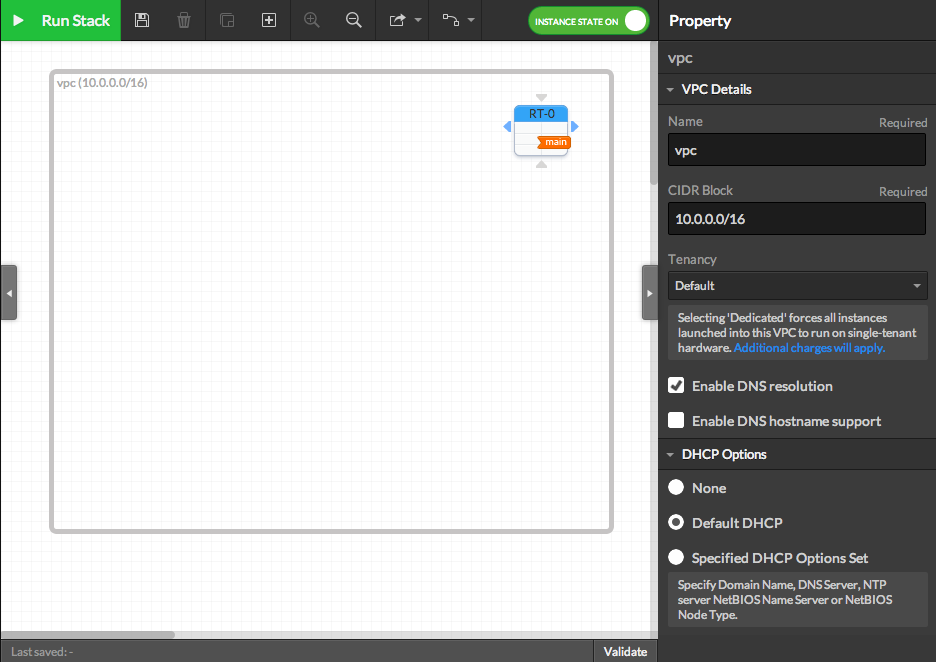
- A default VPC is created when you create a new VPC Stack, as well as a default Route Table.
You can optionaly edit the subnet details in the right panel (don't forget to focus on the subnet by clicking on its blank area). The network address must be written following the CIDR notation:
- You can now add a new Availability Zone of your choice by drag-n-drop it from the left panel:
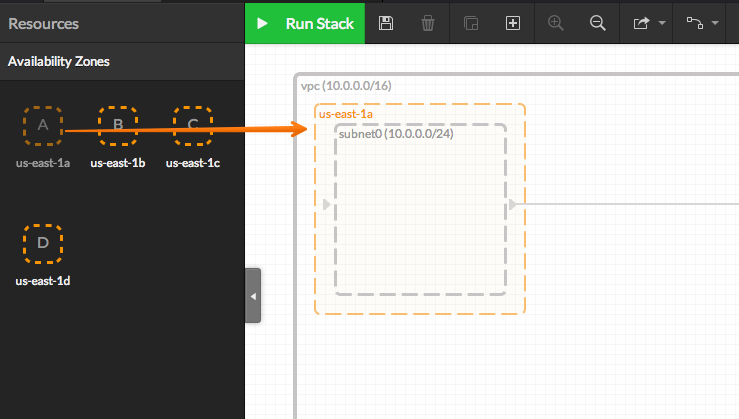
- When adding a new Availability Zone, a default subnet is created.
You can edit the subnet properties in the right panel
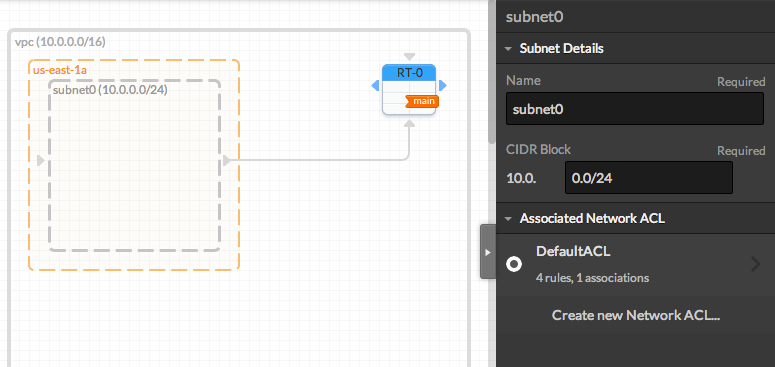
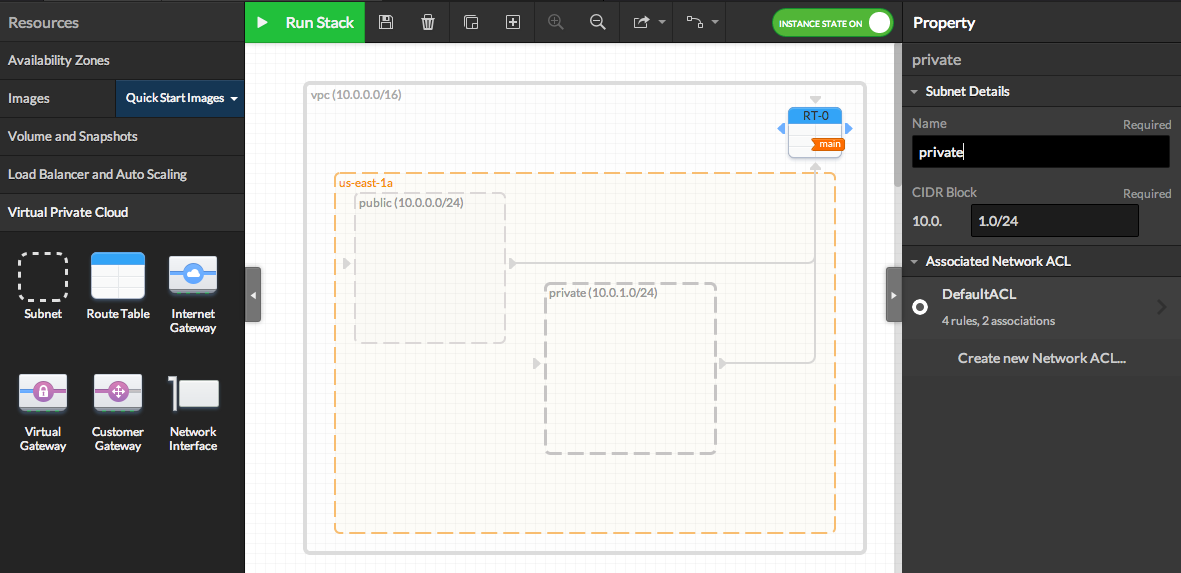
Note that all Subnets are automatically connected to the Main Route Table. Subnets must be connected to only one Route Table. - Add another subnet by dragging it from the resources panel and dropping it in the Availability Zone.
Name one subnet "public" with the CIDR IP "10.0.0.0/24" and the other "private" with the CIDR IP "10.0.1.0/24" as following:
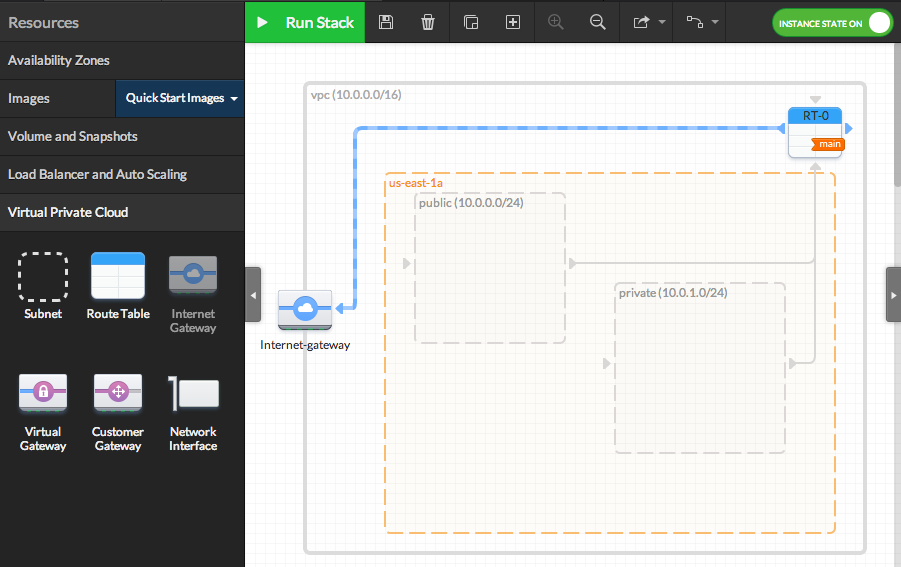
- Add an Internet Gateway and connect it to the Route Table
Drag an IGW from the resource panel (VPC category) to anywhere within the VPC. Note that the IGW will automatically snap to the left edge of the VPC and you can only have one IGW per VPC.
Then, drag from the blue ports on the Route Table to the blue incoming port on the IGW to connect it.
- You can click on the Route Table to define routing rules. Note that when you connect an RT to an IGW we will automatically add a destination "0.0.0.0/0" rule.
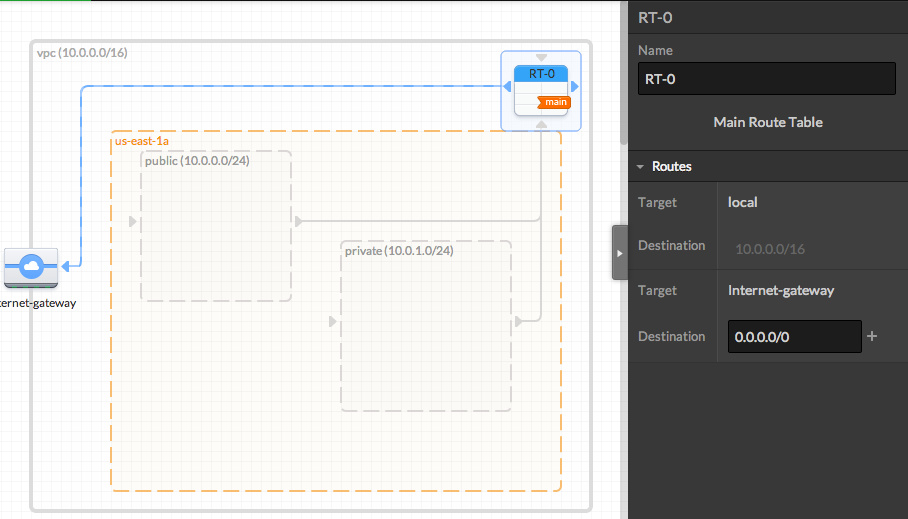
- Add another Route Table
Drag another RT from the resource panel to anywhere in the VPC. We can then associate subnet "private" to this RT by dragging from the grey port on the right of the subnet to an incoming grey port on the RT. Note that, as subnets can only be associated with one RT, the previous association will automatically be removed.
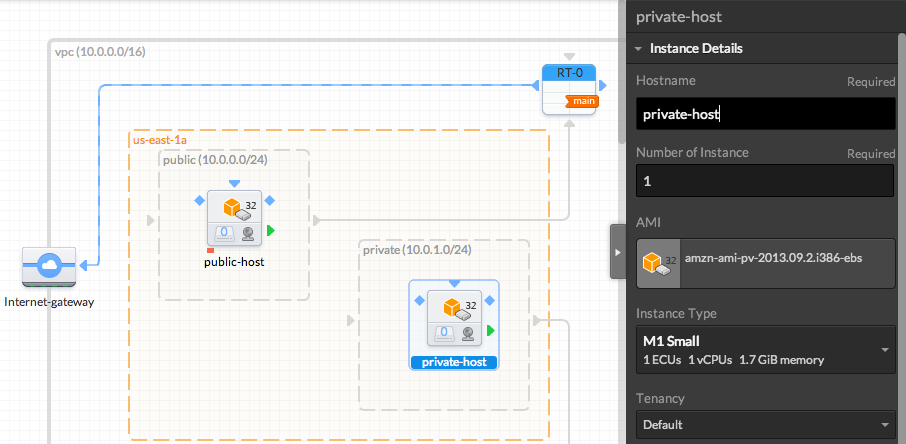
- Add the AMIs to the Subnets
We can now drag on some AMIs from the resource panel to inside the Subnets in our VPC.
Let's start by dragging two Amazon Linux AMIs, one to each subnet. Optionally, click on the instances to rename the hosts in the right panel.
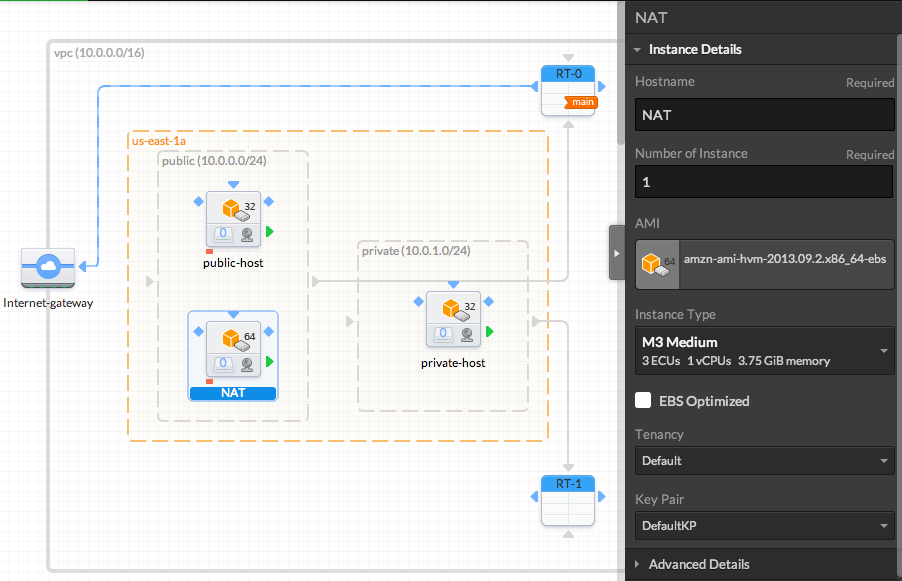
Also add a NAT instance to the "public" subnet. You can find a Amazon Linux NAT AMI in the Quickstart AMIs. Drag it to the public subnet and name it "NAT".
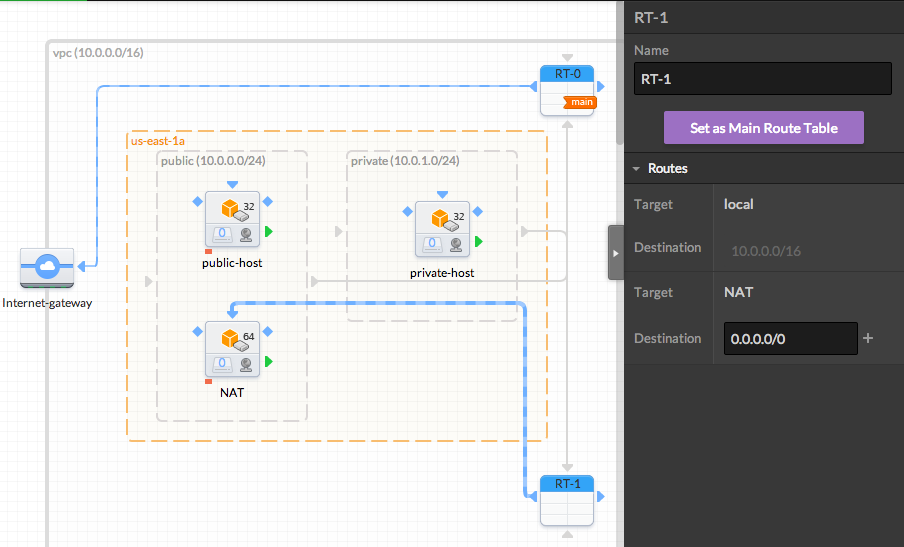
- Connect the NAT and configure the RT
Connect the RT to the NAT AMI by dragging from its outgoing blue port to the incoming blue port on the left of the NAT AMI.
Enter "0.0.0.0/0" as "Destination" in the right panel.
- Configure the AMI IPs
Click an AMI and select "Network Interface Details" in the right panel. Here you can manually specify the IP address within the subnet range (".x" means auto assign random IP) and click the icon on the right to add an Elastic IP to a private IP.
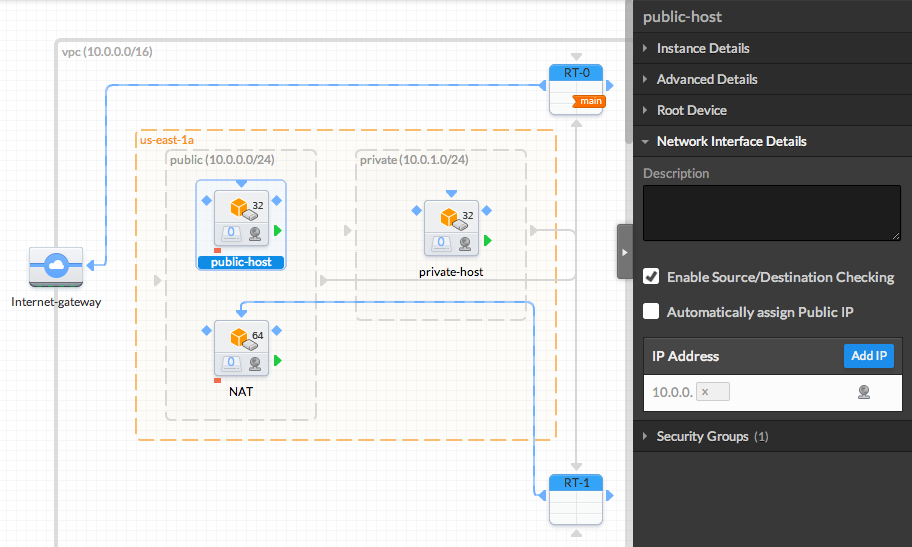
Go ahead and use the following IP configurations:Subnet Host Private IP Elastic IP public-host NAT 10.0.0.x Yes public-host public-host 10.0.0.5 Yes private private-host 10.0.1.5 No - Create and Configure Security Groups for each AMI
Click an AMI and select "Security Groups" on the right panel. Here you can create some new Security groups.
Configure the Security Groups as following:
You can now add the following rules to the Security Groups (see the IDE documentation for more details about security groups):AMI SG Name NAT NATSG public-host WebServerSG private-host DBServerSG SG AMI Security Group Rules In / Out Soure / Dest Protocol Port Range WebServerSG public-host In 0.0.0.0/0 TCP 80 0.0.0.0/0 TCP 443 Your network’s public IP address range TCP 22 Your network’s public IP address range TCP 3389 Out 0.0.0.0/0 TCP 80 0.0.0.0/0 TCP 443 private.private_ip_address TCP 1433 private.private_ip_address TCP 3306 DBServerSG private-host In public.private_ip_address TCP 1433 public.private_ip_address TCP 3306 Out 0.0.0.0/0 TCP 80 0.0.0.0/0 TCP 443 NATSG NAT In 10.0.1.0/24 TCP 80 10.0.1.0/24 TCP 443 Your network’s public IP address range TCP 22 Out 0.0.0.0/0 TCP 80 0.0.0.0/0 TCP 443