VPC with a Private Subnet Only and Hardware VPN Access
Description:
The configuration for this scenario includes a virtual private cloud (VPC) with a single private subnet, and a virtual private gateway to enable communication with your own network over an IPsec VPN tunnel. There is no Internet gateway to enable communication over the Internet. We recommend this scenario if you want to extend your network into the cloud using Amazon's infrastructure without exposing your network to the Internet.
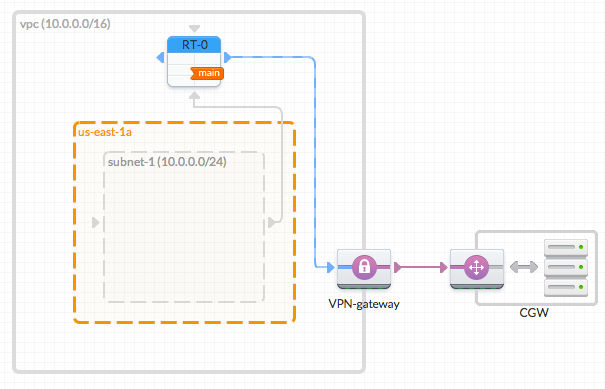
The following diagram shows what we will create in this example:
Steps:
- Create a new VPC Stack, in the region of your choice:
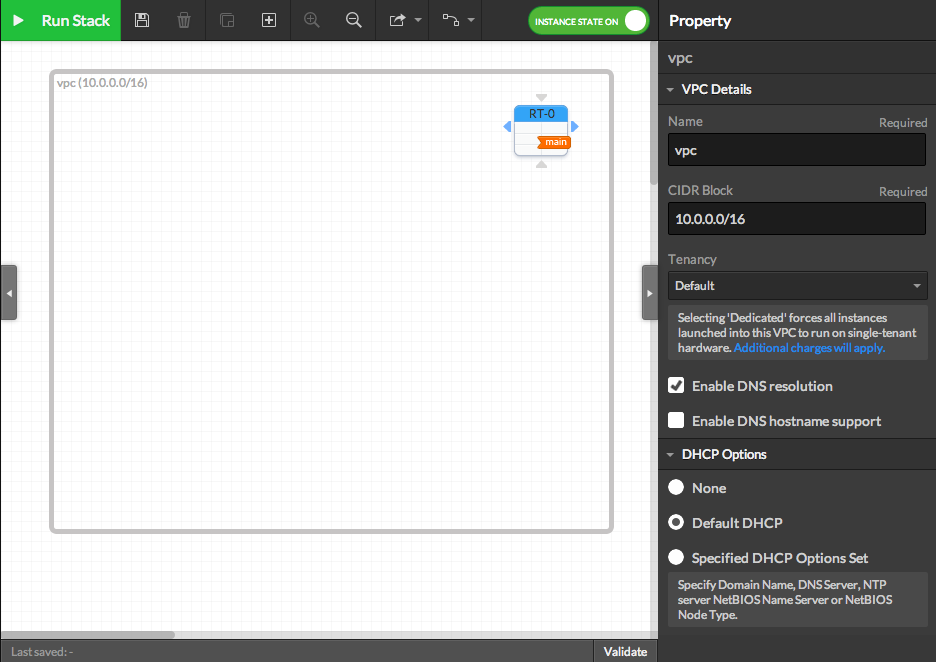
- A default VPC is created when you create a new VPC Stack, as well as a default Route Table.
You can optionaly edit the subnet details in the right panel (don't forget to focus on the subnet by clicking on its blank area). The network address must be written following the CIDR notation:
- You can now add a new Availability Zone of your choice by drag-n-drop it from the left panel:
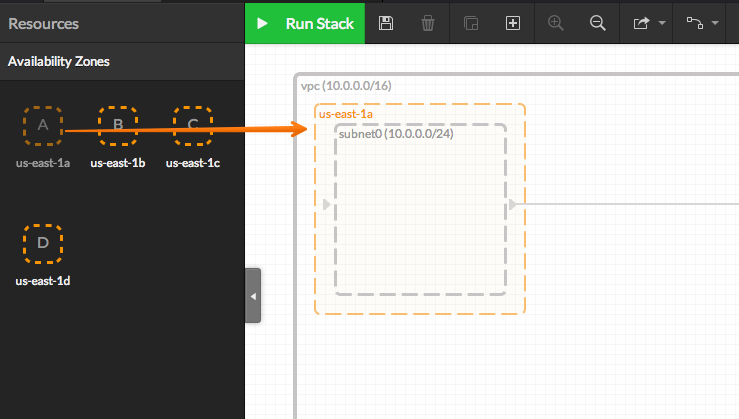
- When adding a new Availability Zone, a default subnet is created.
You can edit the subnet properties in the right panel:
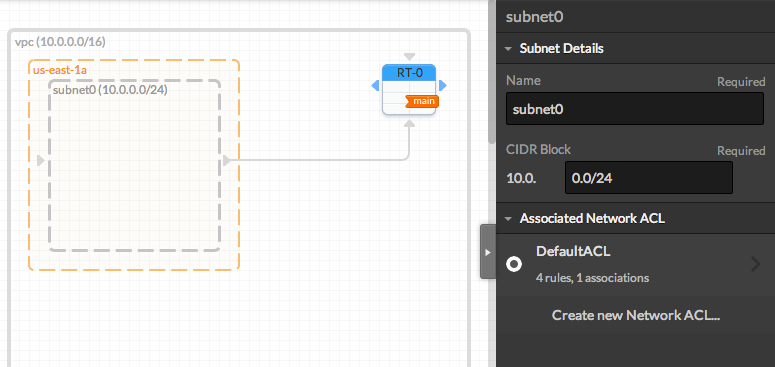
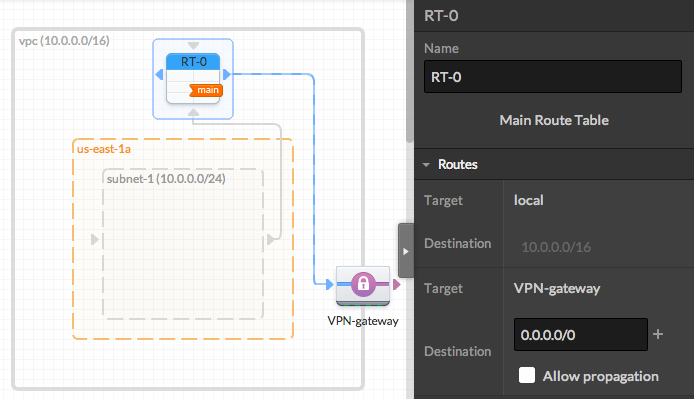
Note that all Subnets are automatically connected to the Main Route Table. Subnets must be connected to only one Route Table. - Add a Virtual Private Gateway and Connect it to the Route Table
Drag a VGW in to the VPC. Note that it will snap to the right side of the VPC. Once added, connect the left blue port of the VGW to the blue incoming port of the RT. Then, enter the Destination "0.0.0.0/0" in the right panel.
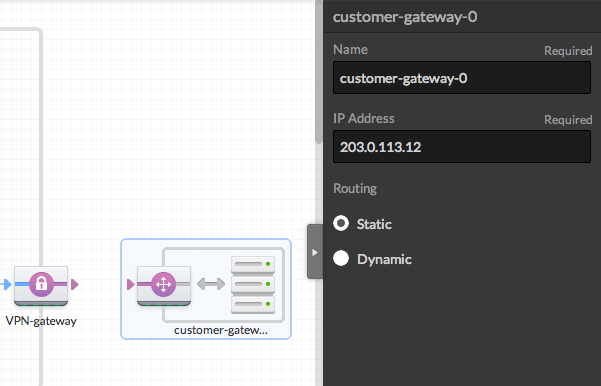
- Add a Customer Gateway
Drag a CGW to the canvas. Note that it must be outside the VPC. After have added the CGW you must enter the IP address of your CGW, e.g., "203.0.113.12". You can rename it as you wish.
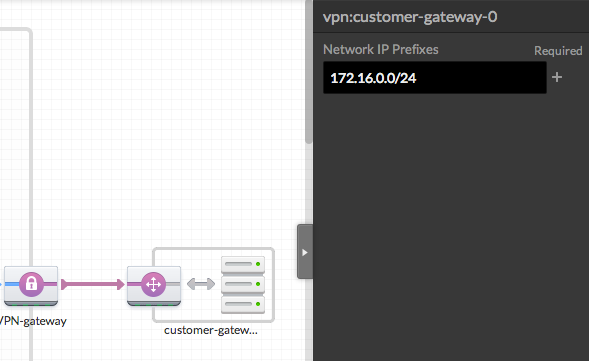
- Connect the CGW and VGW with a VPN Connection
Connect the purple ports of the VGW and CGW to create a VPN. You must enter your VPN CIDR, e.g., "172.16.0.0/24", in the right panel.